Hey readers,
I have one more blog topic for December to round out the year. I am covering the Password Policies Function. I totally forgot that this was added to Sage X3. So, I know starting around version 12 patch 16 (2019R1) (I am pretty sure its in V11 but I will have to make sure later) there was a newer function added. It was called Password Policies. This new function allows you to apply policies to passwords for users with basic authentication. Under Password Policies, you will be able to set restrictions like password length, complexities like upper case/lower case, and stuff like that. This is somewhat new to Sage X3. The old versions like V6.5 had an area where you could do some of that stuff like password expiring stuff. But now, you don’t have to use all those fancy secondary auth apps like SAML2 or oAuth or LDAPs or anything. I mean, unless you want to, because I know some of you IT-ADMINS like that stuff.
And this is how it works:
Log in as the admin account and what I mean is the login is ADMIN and not an account with admin rights. The Admin password better not be admin too or we already have a problem. What you want to do is go to Administration, Administration, Settings, Password Policies. It will be right about here (screenshot!)

Once you actually get in, you will see something like this.
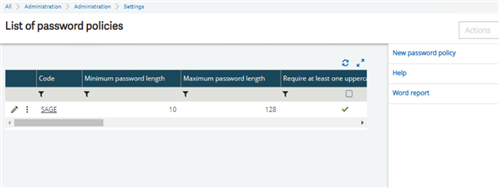
It should be blank, but I already have stuff there and I didn’t feel like removing it. You will want to click on the “New password policy” button to start your new password policy. You can create more than one policy, just in case you didn’t like the first one. This way you can swap whenever you like to and confuse all your users (not sure why the function allows more than one entry, but sure go for it).
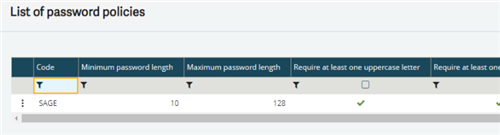
Here, you can see, in this screenshot you can review all the options that are available to use for the password policy.
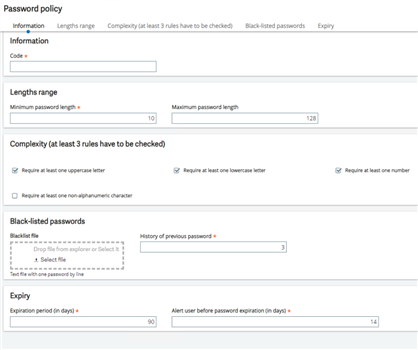
All the options are all pretty much self-explanatory. But if you don’t understand anything here, the online help can help you out. I have also included the online help topic to the blog post just in case you cannot find it. It will be listed at the end of my blog.
Anyways, you select all the stuff you want, add any blacklisted words or phrases you need blacklisted (totally optional) and save. It should look something like mine. I just checked everything
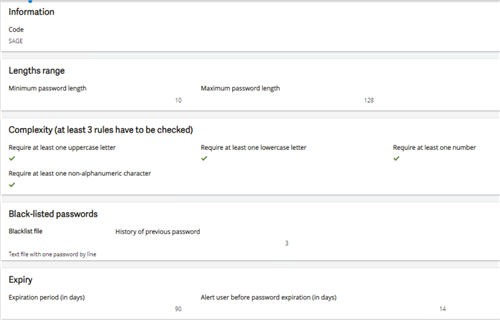
Now that its saved, we have to apply it to the global settings to have that apply it to all users. Note when you apply it to the users, it will affect all users including the ADMIN account. Users currently logged in won’t see the change until they sign out and back in.
To apply it globally, you’ll want to head over to Administration, Administration, Settings, Global settings function.
It should look like this. Click the edit button from the right side
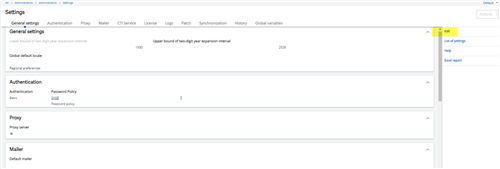
This should open it up for changing. You will see a field labeled “Password Policy”. Click the lookup and select your password policy you just made.
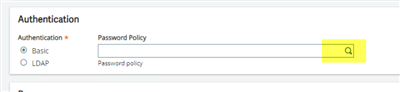
Then click save once you are done.
Now sign out and back in again. It should prompt you to put in a newly updated password.
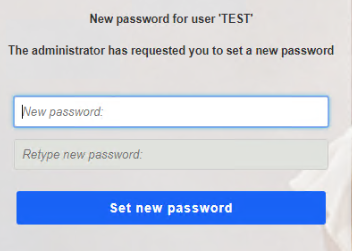
When I try to use the password 1234 it says the following

(checked all the checkboxes)
And there you have it. You can now have more complex passwords without having to setup or use LDAP, SAML2 or oAuth2 or any other authentication base application.
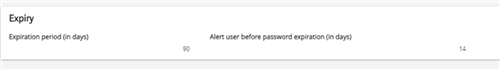
A side note to all of this. If the use has the checkbox checked for “Password Never Expires” on their Administration, Administration, Users, Users profile; this will supersede the expiry section of the Password policies setup.
(This section right here).
P.S.
Here is the online help topic I promised. Sorry but the URLs were stripped when I copied and I’m not going to add them back in, mainly because it’s way to tedious to do.
Password policiesIntroduction This feature enables you to define a password policy on the signature code in order to ensure the compliance with CFR-21 Part 11 regulations. The signature code is like a secondary password usable by the corresponding API to control field entry on sensitive information. This signature code is managed by the Enterprise Management platform (EMP). It is used when the main password management is outsourced to authentication providers. More information about this feature is given in the following document. A consequence of this feature is that the other password managed by the EMP (the main password used for the database authentication) will also benefit of the password policy. The password policy must be defined in the Global settings in order to be activated. Description The password policies screen includes the following sections: Information Lengths range Complexity Black-listed passwords Expiration Information Code This is the name of the password policy. Lengths range Minimum password length Set here the minimum number of characters the password should contain. The shortest length possible is 6 characters. Maximum password length Set here the maximum number of characters the password should contain. You can choose a password length up to 128 characters. Complexity (at least 3 rules must be checked) You must select at least three rules the password must follow among the ones beneath: - require at least one uppercase letter - require at least one lowercase letter - require at least one number - require at least one non-alphanumeric character Black-listed passwords Blacklist file You can import here a text file with a list of forbidden passwords. In the text file, be careful to write only one password per line. History of previous password For security reasons, it is important not to re-create old passwords. You can set here the necessary number of password changes before being able to choose a password already used previously. Expiration Expiration period (in days) Define here the number of days before the password expires. It is also possible to disable the expiration period for a user. Alert user before password expiration (in days) Indicate here how many days before the password expires the user is told to change it.
|

